Online Education Program for Creative Talent
College of Engineering
Be the true leader of this era who practices love.
Hacking & Security
Training information security experts to respond to cyber attacks
The educational objective of the department is to train experts through the use of practical theoretical and application that will enable them to discover vulnerabilities in information systems and determine appropriate security measures.
Educational Objective
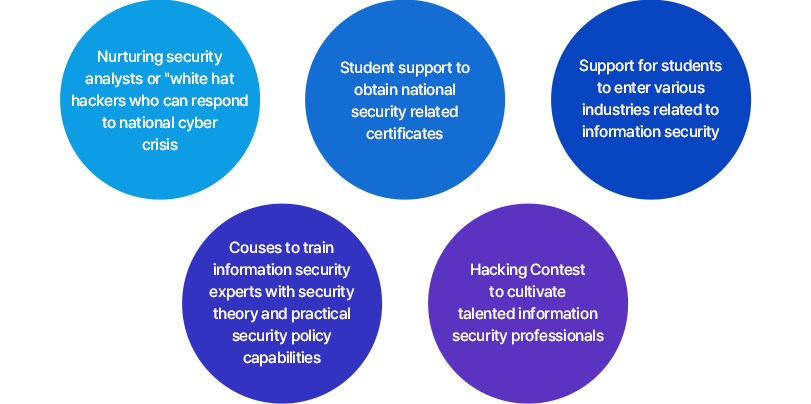
The educational objective of the Department of Hacking and Security is to cultivate experts who possess the theoretical knowledge and practical skills needed to create defense measures by discovering vulnerabilities in information systems, and to train information protection experts who can respond to cyber attacks by providing cyber infringement and personal information infringement incident responses, cyber infringement evidence collection, information protection consulting, and the appropriate security control personnel.
Department Features
Training multi-disciplinary information
security experts with theoretical and practical skills
Support Benefits and Education Features
The Department of Hacking and Security aims to cultivate high-level hacking security experts through a variety of hands-on activities including participation in a professional network consisting of top-notch security company experts. Among the activities the department offers are various offline special lectures and field trips to help students gain insight into various aspects of the complicated and complex world of hacking and security.
Characteristics of Education Infrastructure
- Responding to cyber crises at the national level
- Cultivation of security experts with a thorough grasp of security policy issues
- Support for obtaining national security-related certificates
- Promoting professionalism through relevant education and training
- Hacking contest to train talented information security personnel
- Nurturing professional talent with a systematic approach to learning
- Providing various kinds of information about information security
- Assistance for preparation for graduate school
Major-related Certificates
| Qualification | Summary | Related Subjects |
|---|---|---|
| Information Security Engineer Information Security Industry Engineer | A national official private certificate that certifies the capabilities of the recipient to develop information security systems and solutions, operate and manage major computer operating systems, work with network equipment and information security equipment, establish information security policies for each field, and create and manage security measures all in compliance with laws and regulations related to information protection based on theoretical and practical knowledge of information security | Security Element Technology, Network Security, Application Security, Hacking and Security, Information Security Management and Regulations, Information Security Practice |
| CISSP (Certified Information System Security Professional) | An internationally recognized certificate that certifies the recipient’s ability to lead and unify the work of eight business areas including security and risk management, asset security, security engineering, communications and network security, identity and access management, security assessment, security operations, and software development security, and to maintain professionalism through continuous education | Computer Networks, Network Security, Hacking and Security, Security Element Technology, Encryption Basic Technology, Information Security Audit |
| CISM (Certified Information Security Manager) | The recipient possesses common knowledge of systems of information security and fully understands and can apply mutatis mutandis for information security management. Information security management is an internationally recognized certificate that certifies the work ability of the recipient for information risk management, information security governance, information security program development management, incident response and management. | Security Control and Consulting Techniques, Security Evaluation and Analysis Techniques, Information Security Audit |
| ISMS (Informaion Security Management System) | A nationally recognized private certificate that certifies the ability to conduct certification screening by participating as an examine in the process by which the Internet Promotion Agency or the certification body checks whether the information protection management system of the certification applying agency meets the certification standards through written and on-site examination | Security Control and Consulting TechniqueS, Security Evaluation and Analysis TechniqueS, Information Security Audit |
| PIMS (Personal Information Security Management System) | A nationally recognized private certificate that certifies the ability of the recipient to conduct certification screening by participating as an examiner in the process by which the Internet Promotion Agency or the certification body checks whether the information protection management system of the certification applying agency meets the certification standards through written and on-site examination | Personal Information and Copyright Protection, Security Control and Consulting Techniques, Security Evaluation and Analysis Techniques, Information Security Audit |
| Hacking Security Expert Level 1, Level 2, Level 3 | A private certificate, and Level 1 certifies the recipient’s technical work skills such as planning, research, analysis, investigating, and technology management based on advanced professional knowledge and practical experience; Level 2 certifies the possession of complex functional work skills based on basic theoretical knowledge of hacking security and skilled functions required for practical practice; Level 3 certifies the possession of real-life information protection skills based on basic knowledge of hacking and security, legal system, and ethics | Security Element Technology, Network Security, Application Security, Hacking and Security, Information Security Management and Regulations, Information Security Practice, Information Security Audit |
| GCIH (GIAC Certified Incident Handler) | An internationally recognized certificate that certifies the recipient’s ability to appropriately respond to incidents including detection of malicious applications and network activities, identification of system hacking techniques, detection and analysis of system and network vulnerabilities, identification of causes of accidents, and improvement of business processes based on knowledge of common attack techniques, vectors, and tools | Hacking Response Practice, Information Security Practice, Security Element Technology, System Hacking Practice, Encryption Basic Technology |
| CPPG (Certified Privacy Protection General) | A private certificate that certifies the recipient’s ability to establish personal information protection policies of companies and public institutions based on knowledge of personal information protection-related laws and technologies, and certifies the recipient’s knowledge of personal information handling and management capabilities | Privacy and Copyright Protection |
| CEH (Certified Ethical Hacker) | An internationally recognized certificate that certifies that the recipient is an ethical hacker who is employed by an institution and is suitable to conduct legitimate penetration tests and/or mock hacking | System Hacking Practice, Hacking Response Practice, Security Element Technology, Encryption Basic Technology, Network Security, Network Attack Technique |
| Digital Forensics Expert Level 1 | A private certificate that certifies the ability of the recipient to command and manage tasks such as disk forensics, DB forensics, network forensics, mobile forensics, and application of evidence law | Introduction to Cyber Investigation, Digital Forensics, Information Security Audit, Information Security Management and Regulations |
| Digital Forensics Expert Level 2 | A private certificate that certifies the ability of the recipient to collect digital evidence based on the knowledge of laws related to digital forensics, computer structure, digital storage medium, operating systems, file systems, application programs, computer networks, databases, and ability to produce valid outcomes as evidence of the trial process by creating copy images | Introduction to Cyber Investigation, Digital Forensics, Information Security Audit, Information Security Management and Regulations, Operating System, Linux, Database |
| CCFP (Certified Cyber Forensic Professional) | An internationally recognized certificate that certifies the ability of the recipient to command and control work such as support for crime investigation and law enforcement, respond to cyber crimes targeting public and private organizations, corporate information security, e-discovery necessary for litigation, cyber confidentiality analysis based on knowledge of principles of law and ethics, investigation, forensic science, digital forensics, applied forensics, and the latest convergence security technologies | Introduction to Cyber Investigation, Digital Forensics, Information Security Audit, Information Security Management and Regulations, Operating Systems, Linux, database |
| Engineer Information Processing, Industrial Engineer Information Processing | A national certificate that certifies the ability of the recipient to perform tasks such as planning, analysis, design, implementation, testing, operation, maintenance, etc. as a and performs project work throughout the life cycle of information systems | General Information on Electronic Calculators, Operating Systems, Computer Structure Theory, Data Structure Theory, Database Practice, Algorithm Practice, Computer Networks |
| CCNA (Certified Computer Network Architect) | An international private certificate that certifies the ability of the recipient to install, operate, and repair small and medium-sized corporate networks based on knowledge and skills such as WAN access, network security, network type and media type selection, routing and switching, TCP/IP protocol stack, IP address management, networking equipment configuration and operation, VLAN, IP routing, IP traffic management, IP access control, P2P connection, frame relay connection, etc. | Computer Networks |
Department Outlook
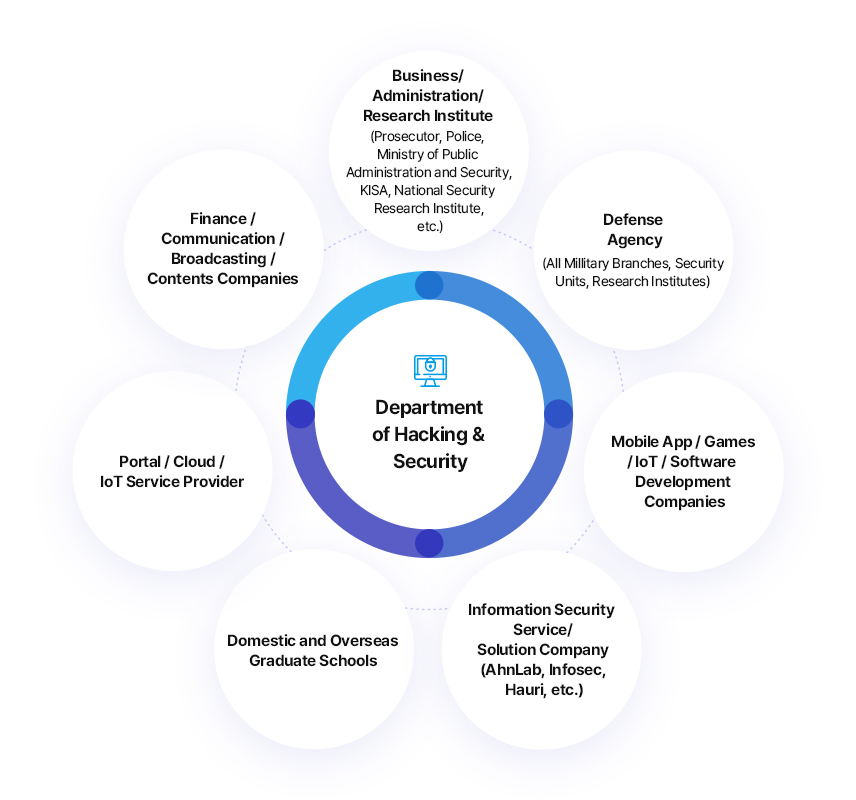
There is increasing demand for information security experts due to rapid growth of domestic and overseas information security markets
Careers after Graduation

HYCU ON/OFFLINE
Programs
- Professional Education Infrastructure
- Understanding of the latest trends through specialized fields of study
- Courses that can be used immediately in practice
- Segmented Professional Tracks
- White hat hacker, cyber investigation, industrial security expert courses
- Training information security experts in various fields
- Useful Online Education
- Smart classrooms where content is available anytime, anywhere
- Support for student discussion classes in a collaborative learning environment
- Support for Online Learning Tailored to Students Needs
- Lectures by type suitable for learning situations including self-study type and practice type
- Flexible lecture schedule that allows for both work and study
- High-quality General Studies Subjects
- Professional educational contents in five areas, including the humanities and sociology.
- Practical subjects available including preparation for obtaining certificates and utilizing programs
Professional Human Networks via OFFLINE Support System
- Master's and Ph.D. degrees
- Guidance on admission to renowned domestic and oversea graduate schools such as Hanyang University and Sejong University
- Scholarship benefits for students attending graduate school of Hanyang Cyber University
- Domestic and Overseas Offline Meetings
- Overseas exposure through special lectures by experts, domestic field trips
- Providing know-how and opportunities for growth according to the characteristics of the major
- Support for Obtaining Various Certificates
- Study support to obtain national and private licenses
- Courses for accredited licenses that are advantageous for employment search and entrepreneurship
- Mentoring Program for New Students
- Sharing of information and support among students through active offline activities
- Operation of programs for both current students and graduates
- Welfare Benefits for Students in Need
- Discounts on medical treatment for students and family members when using the Hanyang University Medical Center
- Support for credit exchange with Hanyang University and use of its various facilities
- Tel
Office Tel. +82-2-2290-0918